Now Reading: Unlocking 127.0.0.1:49342: Your Guide to Localhost and Dynamic Ports
-
01
Unlocking 127.0.0.1:49342: Your Guide to Localhost and Dynamic Ports
Unlocking 127.0.0.1:49342: Your Guide to Localhost and Dynamic Ports

Have you ever stumbled upon the address 127.0.0.1:49342 while working on your computer and wondered what it is? It might appear in a developer log, a network tool, or an error message. Seeing a string of numbers like this can be confusing, but it’s actually a fundamental part of how your computer communicates with itself. This address is not some mysterious external website; it’s a private, internal connection happening right on your machine.
Understanding 127.0.0.1:49342 is key to grasping how software developers test applications, how programs talk to each other, and how your computer manages network tasks efficiently and securely. This guide will demystify this “localhost” address, breaking down what each part means, why it’s used, and what you can do when you encounter it. We’ll explore everything from basic networking concepts to practical troubleshooting steps, giving you the confidence to know exactly what’s happening inside your system.
Key Takeaways
- 127.0.0.1 is “Localhost”: This IP address always points back to your own computer. It’s a special loopback address used for internal communication, meaning network traffic sent here never leaves your machine.
- :49342 is a Dynamic Port: This number represents a temporary, or “ephemeral,” port. Your operating system assigns these high-numbered ports automatically to applications that need to make a network connection without having a pre-assigned port.
- Common in Development: You will often see
127.0.0.1:49342used by local development servers (like Node.js or Python), database clients, and testing tools. It allows developers to run and test applications in a secure, isolated environment. - Security is Important: While localhost is generally safe, it’s crucial to ensure services running on it are not accidentally exposed to the outside world. Firewalls and proper application configuration are essential.
- Troubleshooting is Straightforward: If you encounter issues like “port in use” or “connection refused,” tools like
netstatorlsofcan help you identify which program is using the port so you can manage it.
What is 127.0.0.1? The Loopback Address Explained
At its core, 127.0.0.1 is a special IP address known as the localhost or loopback address. In the world of IPv4 networking, every device on a network needs a unique address to be identified. However, the 127.0.0.1 address is reserved for a very specific purpose: it always refers to the local machine itself. Think of it as your computer’s way of talking to itself. When a program on your computer sends data to 127.0.0.1, that data doesn’t go out to your router or the internet. Instead, it “loops back” internally within your computer’s operating system.
This mechanism is incredibly useful and efficient. It allows different programs on the same machine to communicate with each other using standard network protocols (like TCP/IP) without the overhead or security risks of sending traffic over an external network. For developers, it’s an essential tool for testing web servers, APIs, and other network-dependent applications in a controlled environment before deploying them online. For example, a web developer can run a full version of a website on their local machine, accessible only to them via 127.0.0.1, to find and fix bugs. This keeps the development process private and secure.
The Role of Ports: What “:49342” Means
If 127.0.0.1 is the street address of your computer building, then the number after the colon, :49342, is the specific apartment or office number. In networking, this is called a port. Ports allow a single IP address to handle many different conversations at once. Your computer uses ports to keep track of which data belongs to which application. For instance, when you browse the web, your browser uses port 443 for secure HTTPS traffic. When you send an email, your client might use port 587. These are well-known, standardized ports.
However, the port 49342 is different. It falls into a range known as ephemeral or dynamic ports. These are temporary, non-standardized ports that your operating system assigns on the fly to an application that needs to initiate an outgoing connection. When your browser connects to a website, for example, it is assigned an ephemeral port to receive the reply. The specific range for these ports can vary by operating system but is typically from 49152 to 65535. So, when you see 127.0.0.1:49342, it means some application on your computer is communicating with another local service using a temporary port assigned by your OS.
Common Scenarios for Using 127.0.0.1:49342
You are most likely to encounter the address 127.0.0.1:49342 in specific software development and testing situations. Because 49342 is a dynamic port, it’s often assigned automatically when a client application needs to connect to a server running on the same machine. For instance, a programmer might be running a local web server that listens on a fixed port like 3000. When they open their browser to test it, the browser (the client) is assigned a random ephemeral port, such as 49342, to manage its end of the connection.
Another common scenario involves database connections. A developer might have a PostgreSQL or MySQL database server running locally. When their application code (e.g., a Python script or a Node.js server) needs to fetch data, it establishes a connection to the database. The database listens on its standard port (like 5432 for PostgreSQL), and the application connects from a dynamic port like 49342. This also applies to testing tools, reverse proxies like Nginx configured for local routing, and even some VPN clients that create local network adapters for routing traffic. Seeing 127.0.0.1:49342 in your network logs simply indicates this kind of internal, program-to-program communication is happening.
Practical Examples in Code and Configuration
To make this clearer, let’s look at how developers might configure their applications to use localhost. These simple examples show how different technologies bind to the loopback address.
H4: Node.js Web Server
A developer using Node.js can create a simple web server that listens for connections on their local machine. The server.listen() function specifies the port and, optionally, the IP address.
const http = require('http');
const hostname = '127.0.0.1';
const port = 3000;
const server = http.createServer((req, res) => {
res.statusCode = 200;
res.setHeader('Content-Type', 'text/plain');
res.end('Hello, World!\n');
});
server.listen(port, hostname, () => {
console.log(`Server running at http://${hostname}:${port}/`);
});
Here, the server listens on 127.0.0.1:3000. A client connecting to it would use a dynamic port like 49342.
H4: Python Flask Application
Similarly, a Python developer using the Flask framework can start a local server for testing.
from flask import Flask
app = Flask(__name__)
@app.route('/')
def hello_world():
return 'Hello, World!'
if __name__ == '__main__':
# Binds to 127.0.0.1 by default
app.run(port=5000, debug=True)
When this app runs, it is accessible at http://127.0.0.1:5000. Any browser or tool connecting to it would establish a session from an ephemeral port.
How to Find What’s Using 127.0.0.1:49342
If you discover that 127.0.0.1:49342 is active on your system, you might be curious about which program is using it. This is a common task for developers and system administrators, especially when troubleshooting “port already in use” errors. Fortunately, all major operating systems provide command-line tools to investigate network connections. These tools can tell you the Process ID (PID) of the application holding the port open, allowing you to identify it.
The primary command for this on both Windows and Linux/macOS is netstat (network statistics). Although newer tools exist, netstat is a reliable classic. By using specific flags, you can filter its output to show all listening and active connections, the ports they are using, and the associated process. For example, you can look for any activity involving port 49342. Once you have the PID, you can use another command (like tasklist on Windows or ps on macOS/Linux) to find the name of the program corresponding to that PID. This process helps you confirm whether the activity is expected—like a development server you started—or something unexpected that requires further investigation.
Finding the Process on Windows
On a Windows machine, you can use the Command Prompt or PowerShell to run netstat. The following command is particularly useful:
netstat -ano | findstr ":49342"
Let’s break that down:
netstat -ano: This tellsnetstatto display all active connections and listening ports (-a), show addresses and port numbers numerically (-n), and include the owning process ID (-o).| findstr ":49342": This pipes the output ofnetstatto thefindstrcommand, which filters the results to show only lines containing our target port.
The output will look something like this: TCP 127.0.0.1:49342 127.0.0.1:5432 ESTABLISHED 9876. The last number, 9876, is the PID. To find out what process this is, run:
tasklist /fi "pid eq 9876"
This will show you the name of the executable, like myapp.exe or postgres.exe.
Finding the Process on macOS and Linux
On macOS and Linux, the process is similar, but the commands are slightly different. You can use netstat or the more modern ss command. A very common and powerful tool is lsof (list open files).
To find what’s using the port with lsof:
lsof -i :49342
This command will directly show you the command name, PID, user, and other details about the process using that port.
Alternatively, using netstat:
netstat -anp | grep ":49342"
The flags here are: -a (all), -n (numeric), and -p (show program/PID). The grep command filters the output. You may need to run this with sudo to see the program names for all processes. Once you have the PID, you can get more details with the ps command:
ps -p 9876 -o comm=
This will return the name of the command associated with the PID.
Understanding Port Ranges and Their Uses
Computer networking relies on a standardized system of ports to manage traffic. There are 65,535 available ports for both TCP and UDP protocols, and they are divided into three main ranges. Understanding these ranges helps explain why you see certain port numbers, like 49342, in specific situations. The Internet Assigned Numbers Authority (IANA) is the organization responsible for managing these assignments globally.
The first range, Well-Known Ports (0-1023), is reserved for essential internet services. For example, web traffic (HTTP) uses port 80, and secure web traffic (HTTPS) uses port 443. These are standardized so that computers everywhere know how to connect for common tasks. The second range, Registered Ports (1024-49151), is for applications and services that have registered a specific port to avoid conflicts. Examples include MySQL (3306) and PostgreSQL (5432). Finally, the Dynamic or Private Ports (49152-65535) are for temporary, private use. The port 49342 falls squarely in this range, which is why it’s typically used for short-lived client connections.
Here is a table summarizing these ranges and their common uses:
|
Port Range |
Numbers |
Description |
Example Use Cases |
|---|---|---|---|
|
Well-Known Ports |
0 – 1023 |
Reserved for core system services and standard internet protocols. Requires admin privileges to bind. |
HTTP (80), HTTPS (443), FTP (21), SSH (22) |
|
Registered Ports |
1024 – 49151 |
Assigned by IANA for specific applications to prevent conflicts. Can be used by user applications. |
MySQL (3306), PostgreSQL (5432), Microsoft SQL Server (1433) |
|
Dynamic/Private Ports |
49152 – 65535 |
Used for temporary (ephemeral) client-side connections. Assigned automatically by the OS. |
A web browser connecting to |
When you see a connection on 127.0.0.1:49342, it’s almost always a case of the OS assigning a temporary port from the dynamic range for a local client process.
Security Best Practices for Localhost Services
While 127.0.0.1 is designed for internal communication, it’s not immune to security risks. A service listening on localhost is generally safe from outside attackers because traffic to 127.0.0.1 doesn’t leave the machine. However, there are still important security considerations. The biggest risk is privilege escalation, where malicious software already on your computer could connect to a vulnerable local service to gain more control. Another risk is accidental exposure, where a developer mistakenly configures a service to listen on all network interfaces (0.0.0.0) instead of just localhost, making it accessible to anyone on the same network.
The first rule of localhost security is to bind services to 127.0.0.1 explicitly. This ensures the application only accepts connections originating from the same machine. Secondly, always run local services with the lowest privileges necessary. For example, don’t run a local development web server as the root or administrator user unless absolutely required. You should also use a firewall to control traffic. Even on localhost, a firewall can be configured to block unexpected applications from connecting to ports used by your sensitive services, like a local database.
Limiting Exposure and Using Firewalls
Configuring a service to bind to 127.0.0.1 is the most effective way to limit its exposure. If an application is configured to listen on 0.0.0.0 (or :: in IPv6), it will accept connections from any network interface, including your Wi-Fi or Ethernet adapter. This is great for a public web server but dangerous for a local test database. Always double-check your application’s configuration files. For example, in a PostgreSQL configuration, you would set listen_addresses = 'localhost'.
Beyond proper binding, your operating system’s built-in firewall provides another layer of defense. You can create rules that specify which applications are allowed to accept incoming connections on which ports. For a service on 127.0.0.1:49342, this is less critical since the port is dynamic. However, for a server listening on a fixed port that a dynamic client connects to, firewall rules are essential. On Windows, you can use Windows Defender Firewall with Advanced Security to create inbound rules. On macOS and Linux, ufw (Uncomplicated Firewall) or iptables can be used to set up strict rules that deny all incoming traffic by default and only allow connections to specific, approved ports.
Troubleshooting Common Localhost Port Issues
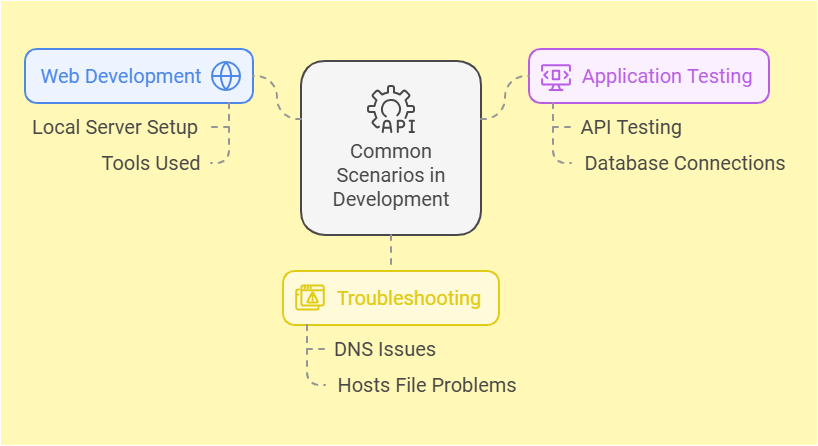
Sooner or later, anyone working with local servers will encounter connection problems. These issues usually fall into two categories: the port is already in use, or the connection is refused. Luckily, troubleshooting these problems on 127.0.0.1 is generally straightforward. A “port in use” error means another program is already bound to the port you’re trying to use. An error like “connection refused” or “site can’t be reached” means that no application is listening for connections on the target port.
When you see an error related to 127.0.0.1:49342, first determine if the problem is on the client or server side. Since 49342 is a dynamic port, the error is more likely to be with the server it’s trying to connect to (e.g., on port 3000 or 5000). The first step is to verify the server is actually running. Check your terminal or command prompt for any error messages where you launched the server. If the server is running, use the netstat or lsof commands discussed earlier to confirm it’s listening on the expected IP address and port. Sometimes, a server might bind to IPv6 (::1) by default, while your client is trying to connect via IPv4 (127.0.0.1).
How to Free Up a Port That Is in Use
If you’ve identified a process that is incorrectly holding a port open, you have a few options. The safest method is to gracefully shut down the application. If you started a server in a terminal, you can usually stop it by pressing Ctrl + C. If it’s a background service, you can use your operating system’s service manager to stop it. For comprehensive guides on various topics, resources like https://forbesplanet.co.uk/ often provide detailed walkthroughs.
If the application is unresponsive, you may need to terminate it forcefully. This should be a last resort, as it can lead to data corruption. First, find the Process ID (PID) using netstat -ano (Windows) or lsof -i :<port> (macOS/Linux).
- On Windows: Open Task Manager, go to the “Details” tab, find the PID, right-click it, and select “End task.” Alternatively, use the command line:
taskkill /F /PID <PID_number>
- On macOS and Linux: Use the
killcommand. The-9flag sends a SIGKILL signal, which forces the process to terminate immediately.kill -9 <PID_number>
Always be certain you are terminating the correct process before running these commands.
Performance Considerations: Localhost vs. Network Traffic
One of the main reasons developers use 127.0.0.1 is for its outstanding performance. When data is sent to the loopback address, it never touches any physical network hardware. There’s no router, no switch, and no network cable involved. The operating system’s networking stack simply redirects the packets from the sending application directly to the receiving application on the same machine. This results in extremely low latency—the delay between sending and receiving data is measured in microseconds, not milliseconds.
This near-instant communication is ideal for applications that require rapid interaction, such as a web application connecting to a local database. For every page load that requires a database query, the delay is minimal, making the development and testing process much faster. In contrast, if the database were hosted on another machine on the local network, or worse, in the cloud, each query would incur network latency, slowing down the entire workflow. Furthermore, localhost communication consumes fewer system resources because it bypasses the drivers and hardware processing associated with physical network interfaces. This efficiency is a key advantage for resource-intensive tasks like running complex test suites or compiling large projects.
Understanding the Differences: 127.0.0.1 vs. 0.0.0.0 vs. ::1
In the world of networking, you’ll often see other special addresses like 0.0.0.0 and ::1. While they may seem similar to 127.0.0.1, they serve very different purposes. Understanding these distinctions is crucial for correctly configuring and securing network services.
- 127.0.0.1 (localhost for IPv4): As we’ve covered, this address always means “this computer.” It is used for sending traffic to your own machine. You can connect to
127.0.0.1, but a server can’t “listen” on it in the same way it listens on0.0.0.0. A service binds to127.0.0.1to ensure it only accepts connections from the local machine. - 0.0.0.0 (The “Unspecified” Address for IPv4): This address is used when configuring a server to listen for incoming connections. When a service is bound to
0.0.0.0, it tells the operating system, “I will accept a connection on any network interface on this machine.” This includes localhost, your Ethernet connection, your Wi-Fi, and any VPN adapters. It’s a wildcard address that means “all available IPv4 addresses on this machine.” This is what you use when you want a service to be accessible from other computers on the network. - ::1 (Localhost for IPv6): This is the IPv6 equivalent of
127.0.0.1. IPv6 is the newer version of the Internet Protocol, designed to replace IPv4. The::1address serves the exact same loopback function, allowing a machine to send packets to itself using the IPv6 protocol. Modern operating systems are dual-stack, meaning they can use both IPv4 and IPv6 simultaneously. Sometimes a service might bind to::1but not127.0.0.1, which can cause connection issues if a client tries to connect using the wrong protocol version.
In summary, 127.0.0.1 and ::1 are for sending traffic to yourself. 0.0.0.0 is for receiving traffic from anywhere.
How Web Browsers Handle Localhost
Web browsers treat localhost and 127.0.0.1 addresses in a special way, recognizing them as secure contexts. This has important implications for modern web development. Many new web APIs, such as Service Workers, Web Authentication, and Push Notifications, require a secure context to function. This typically means the website must be served over HTTPS with a valid SSL/TLS certificate. However, major browsers like Chrome, Firefox, and Safari make an exception for localhost. They treat it as a secure origin, allowing developers to test these powerful features without the hassle of setting up a local HTTPS environment with self-signed certificates.
This special handling streamlines the development workflow immensely. However, developers should be aware of potential issues like mixed content. This occurs when a page loaded over a secure context (like localhost) tries to load resources (like images or scripts) from an insecure http:// address. Browsers will block these requests by default to protect the user. When working with 127.0.0.1, it’s important to ensure all assets are also served locally or from a secure HTTPS source to avoid these blockages. This browser behavior reinforces the idea of localhost as a safe and trusted environment for building and testing applications.
Conclusion
The address 127.0.0.1:49342 may look technical and complex, but it represents a simple and powerful concept: your computer talking to itself. By breaking it down, we see that 127.0.0.1 is the universally recognized address for localhost, and :49342 is just a temporary port assigned by your operating system for a specific task. This loopback mechanism is a cornerstone of modern software development, enabling programmers to build, test, and debug applications in a fast, private, and secure environment.
Now, when you encounter this address in a log file or an application setting, you’ll know exactly what it means. You have the knowledge to identify which programs are using it, troubleshoot common connection problems, and understand the security principles needed to keep your local services safe. Far from being a random string of numbers, 127.0.0.1:49342 is a sign that your computer is working as intended, facilitating the complex dance of communication that makes modern software possible.
Frequently Asked Questions (FAQ)
1. Is it safe if I see a connection on 127.0.0.1:49342?
Yes, in most cases, it is perfectly safe. This address represents a connection between two programs on your own computer. It is commonly used by development tools, database clients, and other legitimate software. Traffic to 127.0.0.1 never leaves your machine, so it is not exposed to the internet. However, it’s always a good practice to use the tools mentioned in this article (like netstat or lsof) to verify which application is using the port if you have any concerns.
2. Why do I get a “Connection Refused” error when trying to access a localhost address?
A “Connection Refused” error means that your request reached the 127.0.0.1 address and the specified port, but no application was listening for a connection on that port. This usually means the server or service you are trying to connect to is not running. Check to make sure you have started your local server and that it didn’t crash or exit with an error.
3. What’s the difference between localhost and 127.0.0.1?
Functionally, they are almost always the same. localhost is a hostname that your computer resolves to the IP address 127.0.0.1 (for IPv4) or ::1 (for IPv6). Think of localhost as a nickname for 127.0.0.1. You can typically use either one in a web browser or application configuration, and it will work the same way.
4. How can I stop a program from using a specific port like 49342?
Since 49342 is a dynamic port assigned to a client, you can’t really “stop” it from being used. A better approach is to manage the server it’s connecting to. If you want to free up a port that a server is using (e.g., port 3000), you must stop the server application. If a process is stuck, you can use its Process ID (PID) to terminate it forcefully with taskkill (Windows) or kill (macOS/Linux).
5. Do I need to configure my firewall for 127.0.0.1:49342?
Generally, you do not need to create specific firewall rules for individual dynamic ports like 49342. However, it is a security best practice to configure your firewall to block all incoming connections by default and only create “allow” rules for the specific server ports you trust (e.g., allow connections to your local web server on port 3000). This helps prevent unwanted applications from being accessed, even on localhost.
6. Can a virus or malware use localhost ports?
Yes. If malware is already running on your computer, it can use localhost connections to communicate with other malicious components or to exploit vulnerabilities in legitimate local services. This is why it’s important to run services with minimal privileges and use a firewall. Keeping your antivirus software up-to-date and practicing safe browsing habits is the best defense against malware getting onto your system in the first place.
7. Why does the port number change every time I run my application?
The port number 49342 is an ephemeral or dynamic port. Your operating system assigns these temporary ports from a large range (49152-65535) for outgoing or client-side connections. Each time a new connection is made, the OS may pick a different available port. This is normal behavior and ensures that there are no conflicts between different applications making connections at the same time.
8. What is the difference between TCP and UDP for localhost connections?
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two different network protocols. TCP is connection-oriented and reliable—it guarantees that data arrives in order and without errors. This is what web servers and databases use. UDP is connectionless and faster but does not guarantee delivery. It’s used for things like video streaming or online gaming where speed is more important than perfect accuracy. Both protocols can be used over 127.0.0.1. The tool netstat can show you whether a connection is using TCP or UDP.